 软件星级:3分
软件星级:3分
Icon2Any是一款专业的图形转换成图片的专业软件,可以让大家修改各种电脑里的图标,而且很多用过的小伙伴们都对IIcon2Any赞不绝口,现在小编带来Icon2Any爆破版和破文,欢迎在巴士下载站下载!
无费话,运行之,看着就不像有壳子的!
OD字串搜索key,得到以下地址,下面的可疑的全部下断点!
Breakpoints
地址 模块 激活 反汇编 注释
004F1228 Icon2Any 始终 PUSH EBX
004F1236 Icon2Any 始终 MOV ECX,Icon2Any.004F1258 Invalid key
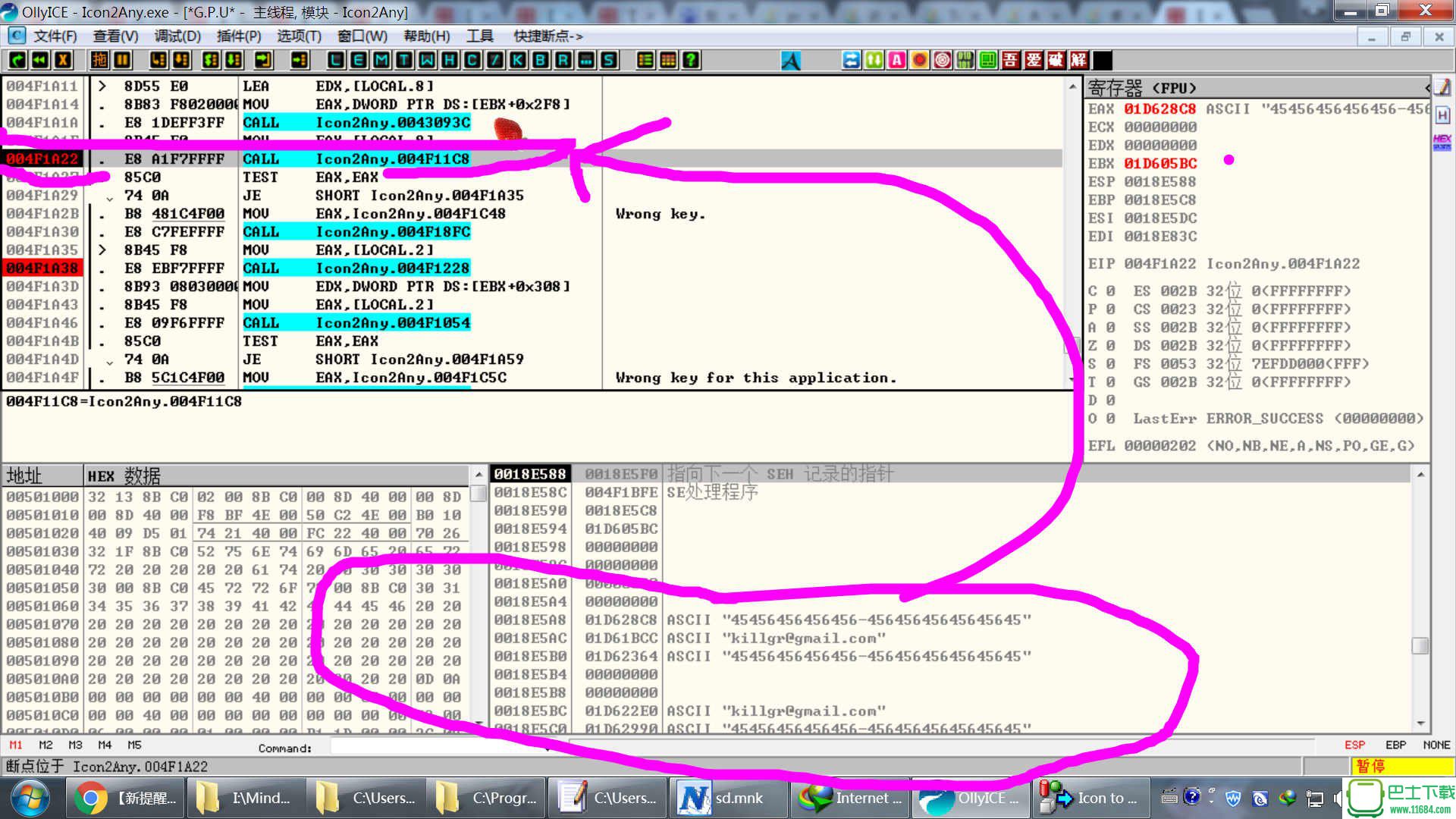
004F1A22 Icon2Any 始终 CALL Icon2Any.004F11C8
004F1A38 Icon2Any 始终 CALL Icon2Any.004F1228
004FC83B Icon2Any 始终 CALL Icon2Any.004FF4F0 333
004FF4F0 Icon2Any 始终 PUSH EBP
004FF549 Icon2Any 始终 MOV EDX,Icon2Any.004FF5C0 SoftwareAha-softIcon2Any
004FF55B Icon2Any 始终 CALL Icon2Any.00462B28 000
004FF562 Icon2Any 始终 JE SHORT Icon2Any.004FF573
004FF566 Icon2Any 始终 MOV EDX,Icon2Any.004FF5E4 Key
004FF81F Icon2Any 始终 MOV EDX,Icon2Any.004FF894 SoftwareAha-softIcon2Any
004FF838 Icon2Any 始终 JE SHORT Icon2Any.004FF847
004FF83A Icon2Any 始终 MOV EDX,Icon2Any.004FF8B8 Key
004F1A22".E8 A1F7FFFF CALL Icon2Any.004F11C8 这个里边的调用 ,二话不说直接F7入后,mov eax,1;ret
004F1A27|.85C0 TEST EAX,EAX
004F1A29 74 0A JE SHORT Icon2Any.004F1A35
004F1A2B|.B8 481C4F00 MOV EAX,Icon2Any.004F1C48 ;Wrong key.

我们向下看
004F1A22".E8 A1F7FFFF CALL Icon2Any.004F11C8
004F1A27|.85C0 TEST EAX,EAX
004F1A29 74 0A JE SHORT Icon2Any.004F1A35
004F1A2B|.B8 481C4F00 MOV EAX,Icon2Any.004F1C48 ;Wrong key.
004F1A30|.E8 C7FEFFFF CALL Icon2Any.004F18FC
004F1A35|>8B45 F8 MOV EAX,[LOCAL.2]
004F1A38|.E8 EBF7FFFF CALL Icon2Any.004F1228
004F1A3D|.8B93 08030000 MOV EDX,DWORD PTR DS:[EBX+0x308]
004F1A43|.8B45 F8 MOV EAX,[LOCAL.2]
004F1A46|.E8 09F6FFFF CALL Icon2Any.004F1054
004F1A4B|.85C0 TEST EAX,EAX
004F1A4D 74 0A JE SHORT Icon2Any.004F1A59
004F1A4F|.B8 5C1C4F00 MOV EAX,Icon2Any.004F1C5C ;Wrong key for this application.
004F1A54|.E8 A3FEFFFF CALL Icon2Any.004F18FC
004F1A59|>B2 01 MOV DL,0x1
004F1A5B|.A1 E8284600 MOV EAX,DWORD PTR DS:[0x4628E8] ;4)F
004F1A60|.E8 830FF7FF CALL Icon2Any.004629E8
004F1A65|.8945 F0 MOV [LOCAL.4],EAX
004F1A68|.33C0 XOR EAX,EAX
004F1A6A|.55 PUSH EBP
004F1A6B|.68 7F1B4F00 PUSH Icon2Any.004F1B7F
004F1A70|.64:FF30 PUSH DWORD PTR FS:[EAX]
004F1A73|.64:8920 MOV DWORD PTR FS:[EAX],ESP
004F1A76|.BA 01000080 MOV EDX,0x80000001
004F1A7B|.8B45 F0 MOV EAX,[LOCAL.4]
004F1A7E|.E8 4110F7FF CALL Icon2Any.00462AC4
004F1A83|.68 841C4F00 PUSH Icon2Any.004F1C84 ;Software
004F1A88|.FFB3 0C030000 PUSH DWORD PTR DS:[EBX+0x30C]
004F1A8E|.68 981C4F00 PUSH Icon2Any.004F1C98 ;
004F1A93|.FFB3 10030000 PUSH DWORD PTR DS:[EBX+0x310]
004F1A99|.68 981C4F00 PUSH Icon2Any.004F1C98 ;
004F1A9E|.8D45 D8 LEA EAX,[LOCAL.10]
004F1AA1|.E8 BEF7FFFF CALL Icon2Any.004F1264
004F1AA6|.FF75 D8 PUSH [LOCAL.10]
004F1AA9|.8D45 DC LEA EAX,[LOCAL.9]
004F1AAC|.BA 06000000 MOV EDX,0x6
004F1AB1|.E8 1A26F1FF CALL Icon2Any.004040D0
004F1AB6|.8B55 DC MOV EDX,[LOCAL.9]
004F1AB9|.B1 01 MOV CL,0x1
004F1ABB|.8B45 F0 MOV EAX,[LOCAL.4]
004F1ABE|.E8 6510F7FF CALL Icon2Any.00462B28
004F1AC3|.8845 FF MOV BYTE PTR SS:[EBP-0x1],AL
004F1AC6|.807D FF 00 CMP BYTE PTR SS:[EBP-0x1],0x0
004F1ACA|.0F84 99000000 JE Icon2Any.004F1B69
004F1AD0|.8B4D F8 MOV ECX,[LOCAL.2]
004F1AD3|.BA A41C4F00 MOV EDX,Icon2Any.004F1CA4 ;Key明显到这里写入注册表
004F1AD8|.8B45 F0 MOV EAX,[LOCAL.4]
004F1ADB|.E8 0412F7FF CALL Icon2Any.00462CE4
004F1AE0|.BA A41C4F00 MOV EDX,Icon2Any.004F1CA4 ;Key 的两次键值!
004F1AE5|.8D4D D4 LEA ECX,[LOCAL.11]
004F1AE8|.8B45 F0 MOV EAX,[LOCAL.4]
004F1AEB|.E8 2012F7FF CALL Icon2Any.00462D10
004F1AF0|.8B55 D4 MOV EDX,[LOCAL.11]
004F1AF3|.8B45 F8 MOV EAX,[LOCAL.2]
004F1AF6|.E8 2526F1FF CALL Icon2Any.00404120
004F1AFB|.0F9445 FF SETE BYTE PTR SS:[EBP-0x1]
004F1AFF|.E8 9882F1FF CALL Icon2Any.00409D9C
004F1B04|.83C4 F8 ADD ESP,-0x8
004F1B07|.DD1C24 FSTP QWORD PTR SS:[ESP]
004F1B0A|.9B WAIT
004F1B0B|.BA B01C4F00 MOV EDX,Icon2Any.004F1CB0 ;Time
004F1B10|.8B45 F0 MOV EAX,[LOCAL.4]
004F1B13|.E8 B412F7FF CALL Icon2Any.00462DCC
004F1B18|.8B8B 14030000 MOV ECX,DWORD PTR DS:[EBX+0x314]
004F1B1E|.8B93 14030000 MOV EDX,DWORD PTR DS:[EBX+0x314]
004F1B24|.8B45 F0 MOV EAX,[LOCAL.4]
004F1B27|.E8 B811F7FF CALL Icon2Any.00462CE4
004F1B2C|.8D55 D0 LEA EDX,[LOCAL.12]
004F1B2F|.8B83 EC020000 MOV EAX,DWORD PTR DS:[EBX+0x2EC]
004F1B35|.E8 02EEF3FF CALL Icon2Any.0043093C
004F1B3A|.8B45 D0 MOV EAX,[LOCAL.12]
004F1B3D|.8D55 EC LEA EDX,[LOCAL.5]
004F1B40|.E8 976BF1FF CALL Icon2Any.004086DC
004F1B45|.837D EC 00 CMP [LOCAL.5],0x0
004F1B49|.8B4D EC MOV ECX,[LOCAL.5]
004F1B4C|.BA C01C4F00 MOV EDX,Icon2Any.004F1CC0 ;UserName
004F1B51|.8B45 F0 MOV EAX,[LOCAL.4]
004F1B54|.E8 8B11F7FF CALL Icon2Any.00462CE4
004F1B59|.8B4D F4 MOV ECX,[LOCAL.3]
004F1B5C|.BA D41C4F00 MOV EDX,Icon2Any.004F1CD4 ;Email
004F1B61|.8B45 F0 MOV EAX,[LOCAL.4]
004F1B64|.E8 7B11F7FF CALL Icon2Any.00462CE4
004F1B69|>33C0 XOR EAX,EAX
004F1B6B|.5A POP EDX
004F1B6C|.59 POP ECX
004F1B6D|.59 POP ECX
004F1B6E|.64:8910 MOV DWORD PTR FS:[EAX],EDX
004F1B71|.68 861B4F00 PUSH Icon2Any.004F1B86
004F1B76|>8B45 F0 MOV EAX,[LOCAL.4]
004F1B79|.E8 0615F1FF CALL Icon2Any.00403084
004F1B7E.C3 RETN
直接mov eax,1
ret 是不行的
只能004F1A29 /74 0A JE SHORT Icon2Any.004F1A35 这里JMP了

F8一种向下,就会达这里,
004F1228/$53 PUSH EBX ;ret这里
004F1229".8BD8 MOV EBX,EAX
004F122B|.8BC3 MOV EAX,EBX
004F122D|.E8 2EFDFFFF CALL Icon2Any.004F0F60
004F1232|.85C0 TEST EAX,EAX
004F1234 74 16 JE SHORT Icon2Any.004F124C ;或是这里jmp了
004F1236|.B9 58124F00 MOV ECX,Icon2Any.004F1258 ;Invalid key
004F123B|.B2 01 MOV DL,0x1
004F123D|.A1 50784000 MOV EAX,DWORD PTR DS:[0x407850] ;碜@
004F1242|.E8 D1A8F1FF CALL Icon2Any.0040BB18
004F1247|.E8 9025F1FF CALL Icon2Any.004037DC
004F124C|>5B POP EBX
004F124D.C3 RETN

如果 你这样的话,下面就会出错,所以jmp掉!

注册表键值被成功写入,但是后面让你重启程序,前面白忙!

重启会 先达这里!
004FF55B".E8 C835F6FF CALL Icon2Any.00462B28 ;000 这里时F7
修改成
00462B28 B0 01 MOV AL,0x1 ;1111111111
00462B2A C3 RETN
结果 还会出注册框,也就是有一个地方的调用很关键
就是这个地方了

这两个调用点直接NOP就好了。
你会说为啥肯定这里呢?

因为下面有【用户】字样
再有F8过不久就会出来让你注册的提示了。
破解好之后 就成下面这个样啦
